Background
When deploying Kong Gateway, there is some data that we do not want to store in plain text, such as connection information to the database. The Kong Secret Manager was developed to solve this problem, which can be solved using a 3rd party service such as AWS Secrets Manager. However, this functionality is unavailable when the environment does not allow connection to external security services. In this case, we can use a encryption tool SOPS, developed by Mozilla to do the encryption and decryption. And also we can make the deploy process into the CI/CD workflow (e.g. Github Action) to make the decrypted configuration file only existing in a temproray workflow.
Preparation
First, let’s try to do the encryption and decryption in a local environment. Install the following necessary tools in your local environment.
SOPS is a handy and popular encryption/decryption tool, supporting PGP, age, Google cloud’s KMS, Azure’s key vault, Hashicorp Vault, etc. We chose age because we intend to use other cloud services as little as possible.
Once you have installed the tools, try age-kengen --help.
| |
Since it looks OK, let’s generate the key.
generate key
| |
Two keys have been generated in the sops-key.txt file: The public key for encryption and the Private key for decryption.
Encryption of configuration file
To use SOPS more conveniently, let’s create a single configuration file, .sops.yaml. You no longer need to specify the key from the command line; enter the Public key you just generated after age, and the encrypted_regex part is where you set which sections of the contents to encrypt.
| |
The following command will encrypt the files in the Kong GW deployment with the above configuration. Parameter -e means encrypt, and -i means save the changes to the orignal file.
| |
The image section is not in the encrypted_regex filed, so it is left in plain text.
Decrypt the configuration file
First, we need to copy the Private Key to .config/sops/age/keys.txt. This is the default path of the private key, so you will not need to specify the Private Key when executing the sops command. Once the Private Key is set, you can compound the file encrypted above with the following command. Similar to the above, parameter -d means dencryption.
| |
After decrypt the config file, we can use is via helm to install to a Kubernetes Cluster.
CI/CD workflow
Next, let’s combian above steps and setup it up into the CI/CD workflow. The configuration file can be deployed without disclosing the plain text configuration file to the user. The decrypted configuration file also exists only in the CI/CD workflow and will be deleted when the CI/CD is finished.
The workflow is as follows.
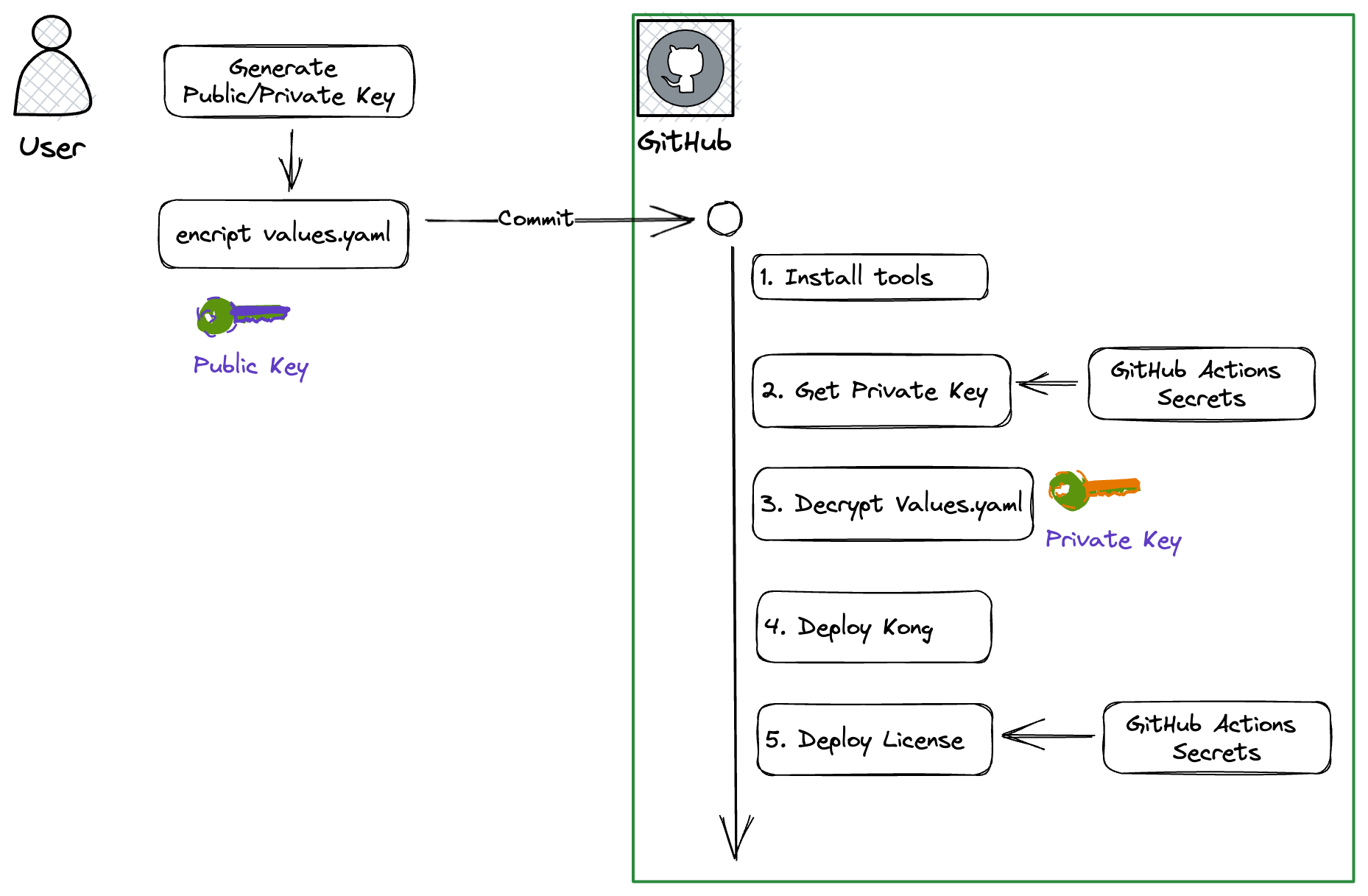
- creation of Public/Private
- encrypt the configuration file
- Commit configuration file
- GitHub Action
- install tools
- Getting Private key
- Decrypt the Configuration File
- Deploy Kong Gateway with helm using the configuration file.
- (Optional) Deploy the license key via Kong Admin API
All steps 1-3 can be done in the local environment. The point is 4-2, Private Key acquisition. If you register the Private Key in advance using the Secrets function of Github Action, you can refer to it directly in the CI/CD workflow. That means you do not have to worry about it being displayed in plain text. Also, please remember that if the Public/Private you use is not a pair, you will get an error when decrypting.
The CI/CD workflow you were writing can be found in [main.yml](https://raw.githubusercontent.com/robincher/kong-mozilla-sops-demo/master/.github/workflows/main. yaml). After committing the encrypted configuration file, you can successfully install Kong Gateway, so please give it a try.
Summary
With CI/CD, after deploying Kong Gateway, there are still many possibilities you can do. For example, create services and routes, or restore the configuration from a backup. Likewise, if there is sensitive information in the configuration that you want to keep encrpied, you can use the same method described above to encrypt it. It’s very simple so please have a try.